The most frequently seen data storage media are USB flash drives and pen drives. They are light, portable and very easy to manipulate and as such, are invaluable tools for transferring and storing data. But at the same time, it is also very suitable not only for unlawful use but also for legal purposes, for the same reasons. In most forensic cases, USB flash drives always hold relevant material evidence. This article is based on USB flash and Pen drive and more focus has been made on how one may easily recover hidden lost data without any issue.
Consequently, electronic gadgets, USB devices and forensic flash drive forensics are quite useful in the analysis of embedded systems, which involve extracting data at a logical level. The forensic process in its most basic sense involves the acquisition of data in flash memory devices using various techniques.
The technical support team is very consistent at it when it comes to problem solving, and during this time also, the query raised by a client, asserting “Kindly help to carry out the recovery of deleted and corrupted data files from Pen Drive for investigation purpose” was also answered, though it seem to be a different way of carving out the files for damaged Pen Drives. The solution says that it is a perfect one for digital forensics, policemen, individuals, and consumption by companies. The basic strategies of investigation have to be done by hand and if necessary the tool is recommended for further investigation.
USB Flash Drive Forensics – Brief Introduction
USB flash drive analysis or USB flash drive investigation is a subset of computer forensics and involves identification, acquisition, examination, and documentation of data within USB flash drives and pen drives. They can hold different forms of data – documents, images, videos, and perhaps banned metadata – all of which can be significant in legal, criminal, or corporate cases.
USB Flash Drive File Systems: Insights into Digital Forensics
When investigating, mostly the latest USB flash drives are incurred, I mean FAT 32. Even some of the old flash drives can also be bought for instance FAT 12/16 this is because Fat refers to the file allocation table used in organising file names of the devices. Typically, there are two copies of the FAT table, as one may become damaged and need the other as a backup. When a file is allocated to this file allocation table, its start cluster is linked to it. All the clusters which belong to different files form the chained clusters.
During the deletion actions on any file from the USB drive or pen drive the first alphabet of the particular file name is replaced by E5 hex which is named as stigma. The cluster which belongs to the erased file is in the operating system and is utilisable but the data contained in the cluster is removed.
A pen drive is usually a flash drive; it is EEPROM (electrically erasable programmable read-only memory) and is non-volatile. This means that it memories the value without storing power and therefore it is dense. Mainly for storage, the behaviour of these ‘flash-memory’ pen drives is not like normal memories such as RAM and disks. If it is the NOR flash, access and writing of data are controlled but if it is the NAND flash the scenario is otherwise.
Core Factors Before Preparing Forensic Investigations
Before any forensic USB investigation is made, one needs to know the algorithm used on the acquired device for storing files. Some of the USB flash drives are simply plugin types that can be utilized on new systems on plugging. However, few editions of Windows systems, such as Windows 98 and other earlier versions, invite a driver for use.
There are some situations which can be met by investigators when, for example, the Pen Drive cannot be recognised in examination machines with the assistance of newer versions like Windows 95, Millennium, Windows 2000, Windows 7, XP, and 98. Such a situation is recommended to check how the flash drive works in another device. However, in another system, it is very much necessary to install a USB hardware write-blocker in order not to allow any transport of data unintentionally between the system and Pen Drive. This is to ensure that there is no change made on this drive and that no form of virus is taken to it.
USB Flash Drive Forensics – Key Procedures to Recover Hidden Lost Data
Investigation of USB drives can be done systematically with the main aim of ensuring they offer accurate results with quality evidence. Here are the key steps:
#1. Identification
The first step is to identify the drive and to describe what it looks like or more specifically, what it is brand name, whom it belongs to, and whether it is a large or small, full or empty, USB. They also search for conduct which may have resulted in physical damage or in attempts to manipulate data.
#2. Collection
The USB drive is traced for proper collection so that data to be captured will not be compromised in any way. They are usually employed in order to prevent unintended manipulation of either side.
#3. Preservation
The original data is retained by capturing a shadow or duplicate copy, at the bit level, of the USB drive. For this reason, the investigation can continue without tampering with the evidence in any way or form.
#4. Analysis
Using specialized forensic tools, investigators analyze the copied data to uncover:
- Hidden files and directories.
- Any data that can be erased with the help of the operating system as long as it’s not overwritten.
- Information in the background of the activity, the time, date, and all activities done by the user.
#5. Reporting
The outcomes are described in the associated report, where all the data retrieved, methods applied, and conclusions drawn are described. This report is usually applied for legal matters.
Recover Hidden Lost Data from USB Drives – Solutions
This is one of the most sensitive steps of USB forensics, by following so, easily recover hidden lost data. Data can be hidden in several forms. In fact any file that has been deleted using normal methods can be recovered if their space has not been overwritten. At times there are hidden partitions and, therefore, the USB drive may contain sensitive information or a virus that is destructive. To hide the data, it can be inserted between other file types as part of image, video, etc. Files may either be made inaccessible by the file system or destroyed by physical means.
#First: Manual Methods To Recover USB Flash Drive Data
Simple methods along with tools are used in manual methods for finding hidden data to recover pen drive data:
1. Using Command Prompt:
- Run the Command Prompt.
- Set up commands like attrib -h -r -s /s /d *.* to unhide files.
2. File System Check:
- To fix file issues with the system as well as recover data, use chkdsk.
3. Exploring Hidden Partitions:
- Hidden partitions can be uncovered using disk management.
However, these methods work well in specific scenarios, but are not capable of restoring files that are heavily damaged or encrypted.
#Second: Professional Pen Drive Data Restorer Solution to Recover Hidden Lost Data
In Pen Drives to extract full data, including the lost data from Pen Drive, the most reliable is Pen drive recovery software application. This application is meant to be a professional one and will do a complete scan on a damaged or corrupted Pen Drive device.
It repairs corrupt flash drives without deleting any file stored on the flash drive. As a tool that guarantees the recovery of data for a forensic investigation, the software is associated with several features. Here the USB thumb drive recovery tool has to be installed on the system as a demo version after which it can be upgraded to a licensed version.
Recover Lost Data from a Pen Drive: Step-by-Step Guide
After the installation of the software, the user need to follow the below mentioned steps:
Step 1: To recover hidden lost data from the pen drive connect the pen drive to the system.
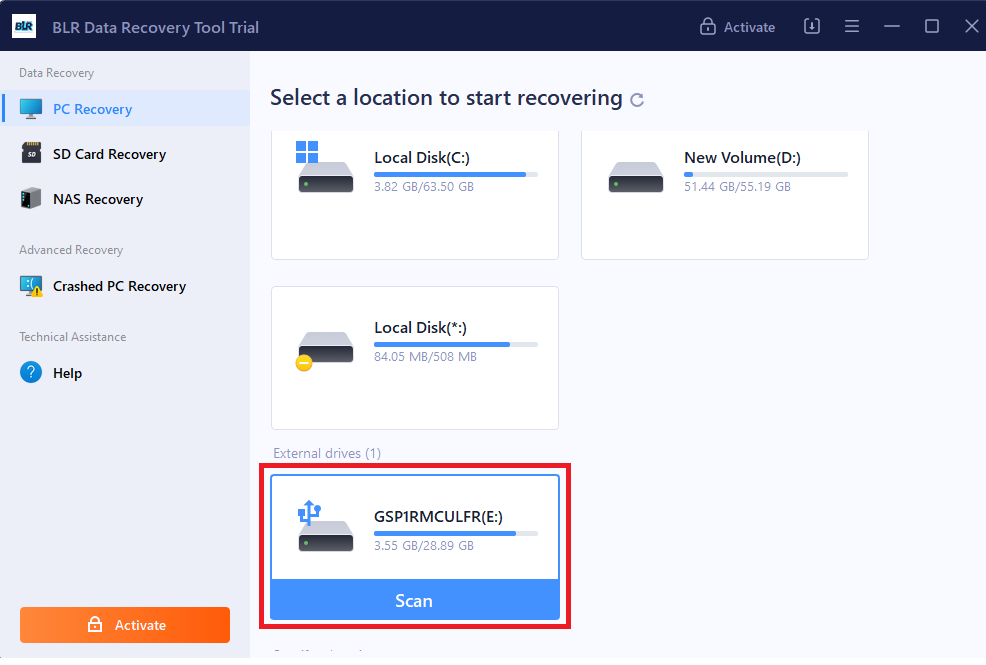
Step 2: Start the scanning process. The tool will scan the drive and show all of the files that can be recovered.
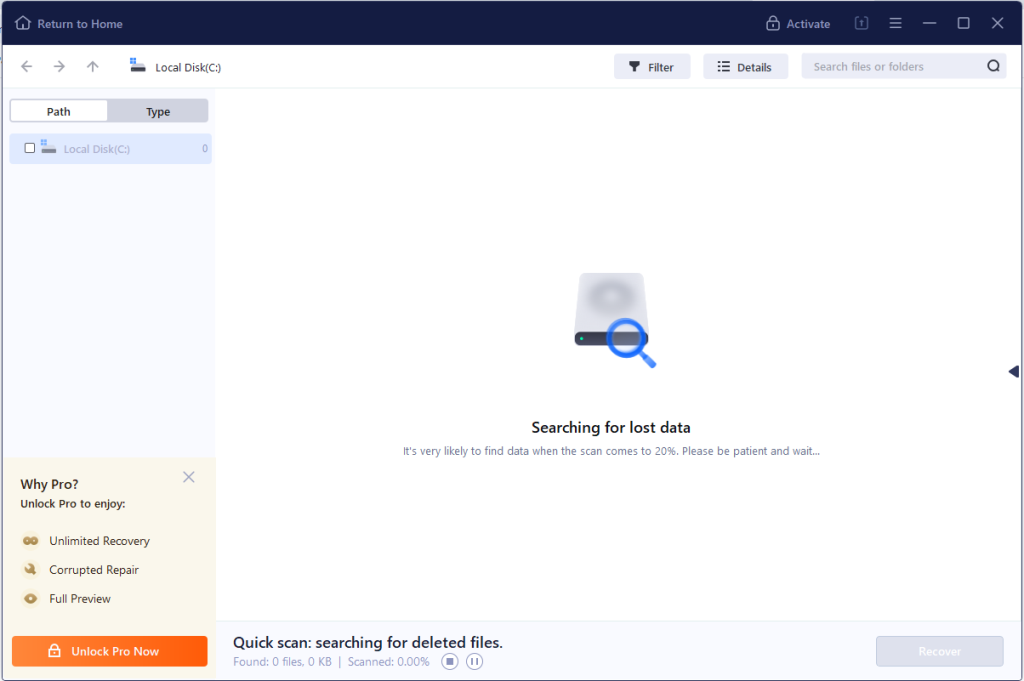
Step 3: Check the files in the preview to ensure that they are perfectly OK, before choosing the appropriate files and then click on the recovery button.
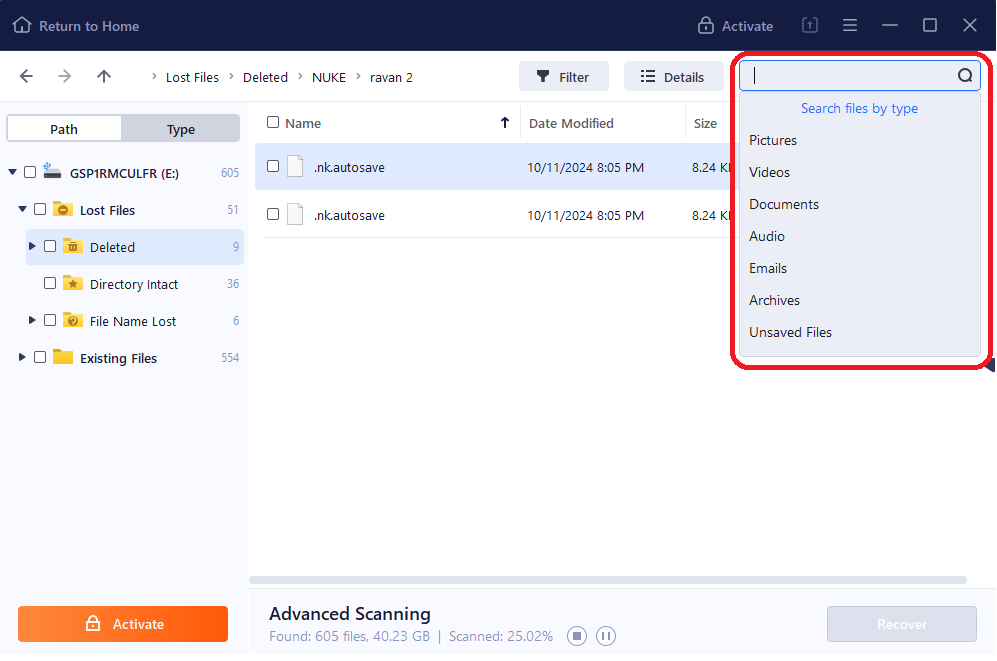
Step 4: Select the data/files to recover back and click on the ‘Recover’ button to complete the process.
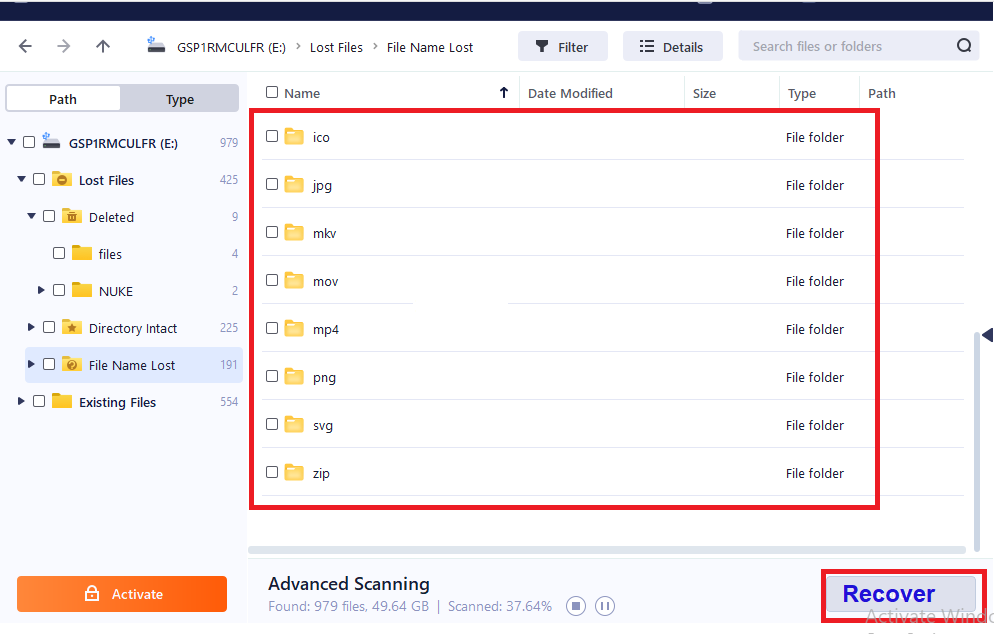
Conclusion
Digital forensics moves on with each and every type of data storage that is found during the investigation. Not even the small storage devices, such flash drives, also referred to as pen drives, are not an exception. At last, it has evolved and begun the field of USB device forensics as well as helpful recovery tools to recover hidden lost data such as USB stick data recovery software to provide essential assistance to law enforcement through pen drive forensic. It can also restore deleted photos off pen drive. This tool is the first and foremost tool for mining closed sources of evidence in the format of data files, the example of which is this tool.
Also read relevant informative articles:
Solution to USB drive shown as ‘No media’


![Restore and Recover Folder Structure Data – Hierarchical File System [Instant]](https://www.blrtools.com/blog/wp-content/uploads/2024/12/Restore-and-Recover-Folder-Structure-Data.jpg)
1 thought on “USB Flash/Pen Drive Forensics : Recover Hidden Lost Data”